
Private Paths Service
What is Private Paths?
A secure system that allows third-party applications to connect without relying on the public internet.
Role
Design lead
Tools
Figma, Adobe illustrator
Duration
10 months
Overview
Many companies are blocked from onboarding new customers because the security specifications that these big, prospective partners require present high barriers to entry. Using a cloud provider to facilitate private connectivity is a much more scalable solution and opens a lot of doors for customers.
We successfully achieved this by utilizing IBM Clouds Network Load Balancer and Virtual Private Endpoint Gateways to connect resources without exposing any traffic to the public internet.

My Role
I took over this project at the mid to high fidelity design phase as design lead, with the goal of facilitating private paths’ beta release. While working on this project, through user testing, I discovered the need for certain features that were initially not considered as well as areas of improvement.
Our Users
There are 2 users private paths is designed for; consumers and providers.
Consumers request private connections for their applications (a healthcare company securely connecting to a third-party provider). Providers receive and manage these connection requests (an independent service provider offering cloud-based healthcare solutions).

Research
A competitive analysis found that setting up private connections on platforms like AWS and Azure were quite difficult, especially when configuring Load Balancers frequently interrupts the user’s workflow. They need to navigate between multiple tabs just to get what the information they need.
Our solution involved streamlining the process, allowing users to create all necessary resources (Load Balancer with Private Path) without leaving their configuration.
Additionally, our competitors needed users to manually accept each connection request, which is quite overwhelming for multiple requests from the same company. Our solution implemented an automation feature to recognize and automatically approve or deny account IDs.

AWS service to service endpoint
Mid-fidelity
Providers begin by configuring and purchasing their Private Path service. Then, they easily access and manage all Paths within their VPC. 100% of participants in the usability testing found this task straightforward.

A Network Load Balancer for Private Paths is needed and typically requires over 20 steps. To streamline the experience, essential fields were pre-populated reducing the process to 4. This enabled all participants to easily set up a Private Path Load Balancer with their service.

Next, the Provider shares the CRN with the Consumer, who enters it on the Virtual Private Endpoint page to start the connection. 90% of users found the preview helpful, and 87% felt confident their CRN was verified correctly.

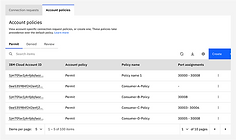
Then, the Provider logs into their Private Path to approve or deny incoming connection requests from Consumers. The interface clearly displayed pending requests and included notifications; 100% of participants found it easy to complete.

With the connection established, the Consumer can securely interact with the Provider’s application. We focused on making connection progress clear and accessible, resulting in 100% of participants successfully viewing and confidently understanding their request status.

High-fidelity
As stated above, providers begin the process by creating their Private Path service. We included a mini tutorial above helping new users through the process.
To do this, the provider needs to select or create a network load balancer. Through testing and multiple iterations, we where able to reduce the steps from 10 to 6, including a tutorial and review page.
Providers could also add automation policies that auto-approves or denies connections from specific accounts. Confidence scores rose from 61/100 to 70/100 with final testing further increasing the score to 82/100.
In total, users rated the entire process a 4.1 out of 5





We introduced the concept of publishing a Private Path i.e keeping services unpublished by default so Providers could edit and test before enabling Consumer access.
Testing revealed user ratings for this feature reduce from 76/100 to 60/100 in terms of difficulty.

At the final stage, once a Consumer submits a connection request to a Private Path, the Provider has the ability to either approve or reject it. This action proved to be highly intuitive; users consistently gave it a perfect ease-of-use score of 100 out of 100. As a result of refinements to the experience, we saw a significant improvement in task completion time, reducing the average from approximately 8 minutes and 52 seconds down to 3.5 minutes; more than half the time it initially took.

Testing feedback
After launch, I gathered feedback from network engineers and architects, who highlighted challenges and potential upgrades on the following:
-
Publishing process: users wanted a more automated publishing process that could verify access rights based on the predefined criteria.
-
Load Balancer: users found the setup unintuitive and suggested a more streamlined approach.
-
ID validator: users recommended an ID validator; it will help providers ensure only authorized users could gain access.
Overcoming Challenges and Enhancing User Experience
This project required adaptability, clear communication, and cross-functional collaboration to address evolving requirements and user needs. By staying agile and user-focused, I helped simplify complex configurations, ensuring a seamless experience for both technical and non-technical users.
-
Adapting to Change: I continuously adjusted to evolving requirements, incorporating feedback from internal teams and external users to refine the product.
-
Clear Communication: I maintained open collaboration with product managers, content designers, and other stakeholders to ensure alignment across teams.
-
Thorough Documentation: I carefully documented each development phase, enabling smooth adaptation to shifting priorities while keeping the project on track.
-
Collaborative Approach: I partnered with network engineers to translate complex technical configurations into a user-friendly experience, ensuring broader adoption.
-
User-Centered Development: I embraced continuous feedback loops to address real-world challenges and improve usability.
-
Looking Ahead: My focus moving forward is on enhancing automation, strengthening access validation, and refining configuration tools based on ongoing feedback.